A Lesson in Mac and Data Security
Over the past few weeks I have had relatives and others ask questions about Macs and viruses, as well as data security regarding Macs and the cloud. I’ve been responding individually, but thought that posting those answers here would be a great idea.
We’ve long ago left the time where the myth that Macs don’t get viruses was believable. They do get viruses. But you still don’t really need to install huge expensive malware scanning products. macOS has a few aspects to it that help prevent viruses from being contracted that not everyone is aware of.
macOS has for a while had a feature called Gatekeeper which restricts what is allowed to run on the Mac without explicit approval to, by default, just Mac App Store apps plus apps digitally signed by Apple-approved developers. You can further restrict your Mac to just apps delivered by the Mac App Store if you want (I don’t know why Apple’s own tech doc linked above hasn’t been updated since the Anywhere option was removed…). I actually have my Macs set to App Store-only, since it is most secure and, well, due to this next part… You can always override the settings for specific apps, but nothing can just run unless it is from a trusted source. Viruses would definitely not be on the Mac App Store, and rarely come from trusted developers, and if they do Apple is quick to pull that trust. This setting is in the Security section of System Preferences (in the Apple menu) if you want to change it. 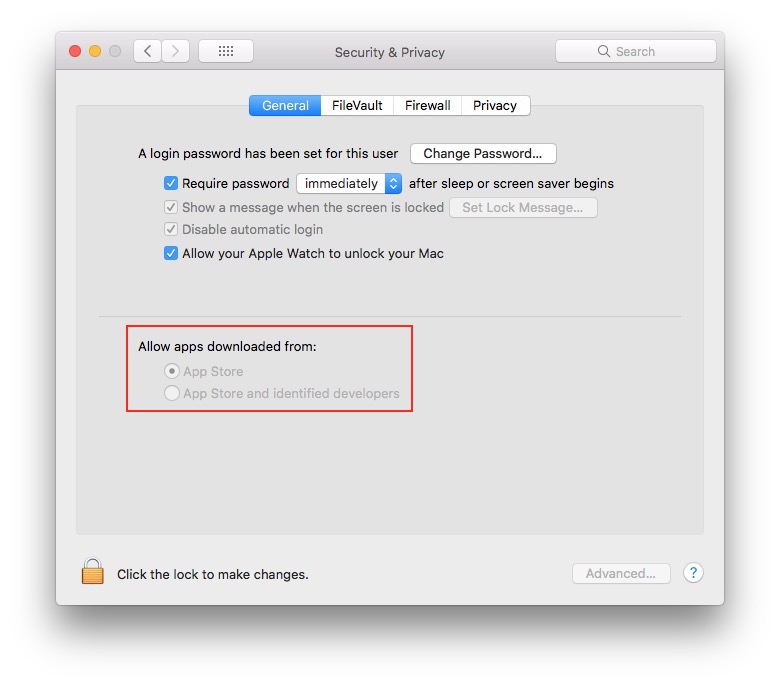 For a little shorter of a time period there has also been a feature called System Integrity Protection. This disallows anything on the Mac other than Apple-signed OS updates from changing anything that is a part of the core OS and Apple software, even if that thing has root administrative privileges (when you type in your password). So viruses, if they did get on your Mac, simply could not modify the OS. SIP also does a number of other things to keep Macs running securely, like only running specially-signed third-party kernel extensions, and only with explicit administrative approval. The only way to change this setting is by booting your Mac to the Recovery OS and typing something in at the command line prompt in Terminal.
For a little shorter of a time period there has also been a feature called System Integrity Protection. This disallows anything on the Mac other than Apple-signed OS updates from changing anything that is a part of the core OS and Apple software, even if that thing has root administrative privileges (when you type in your password). So viruses, if they did get on your Mac, simply could not modify the OS. SIP also does a number of other things to keep Macs running securely, like only running specially-signed third-party kernel extensions, and only with explicit administrative approval. The only way to change this setting is by booting your Mac to the Recovery OS and typing something in at the command line prompt in Terminal.
macOS automatically gets security updates pushed to it from Apple, so long as you keep the appropriate checkboxes selected in the App Store preferences. 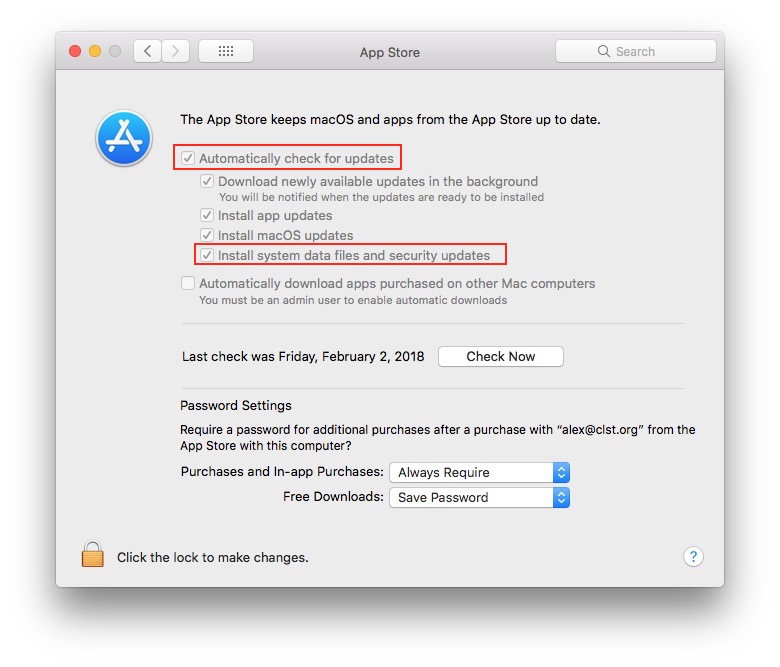 These include updates to Gatekeeper configuration, as well as the built-in virus scanner Xprotect, and the built-in malware removal tool MRT, so long as the Mac is connected to the internet. Apple doesn’t really publicize when updates to these are pushed, but they tend to happen weekly or bi-weekly. If you want to check on what versions of security software and configuration you have I’d recommend LockRattler. Such updates help ensure that your Mac stays secure. Still, also always update to the latest software yourself as new OS releases come out.
These include updates to Gatekeeper configuration, as well as the built-in virus scanner Xprotect, and the built-in malware removal tool MRT, so long as the Mac is connected to the internet. Apple doesn’t really publicize when updates to these are pushed, but they tend to happen weekly or bi-weekly. If you want to check on what versions of security software and configuration you have I’d recommend LockRattler. Such updates help ensure that your Mac stays secure. Still, also always update to the latest software yourself as new OS releases come out.
Any file downloaded to the Mac via Safari, Chrome, Firefox, Mail, or Messages, among other apps, is automatically quarantined and transparently undergoes a security check before it gets opened for the first time. The Mac will insist that you trash any download that fails this check. This is where Xprotect comes in, as part of this check. Gatekeeper is also only triggered on executables that are quarantined. It is partly because of these security checks that I use Apple’s built-in apps wherever I can, or at least use quarantine-aware apps, and recommend the same for others as well.
It is worth noting that these security measures apply to any executables. For most people these will only ever legitimately be apps. For advanced users there will be others you run into, like command-line tools. But under no circumstance should document files (like Word, Pages, Keynote, PDF, JPG, etc.) have executable code. If when opening such a file any of these measures get in the way then definitely be suspicious of the file, its origin, and delete the file. It is also worth noting that Windows executables (.exe) are harmless to the Mac, as the Mac simply isn’t able to run them.
If you still feel like you want some additional virus protection, the only one I’d recommend is the open source ClamAV. This is a command-line engine, so really is for advanced users. Anyone else I think is just fine with the built-in tools, and even advanced users don’t need anything more. Just, if you want something more, that is where I’d look.
Most well-built Mac apps these days, and a requirement of Mac App Store apps, is to be sandboxed. Sandboxing means that the app lives in its own contained universe so it cannot access files that it hasn’t either created or been given explicit access to. I try to make sure that most of the apps I use are sandboxed, but it really isn’t up to users. If somehow a malicous app that is sandboxed got on your Mac it couldn’t hurt anything beyond itself, but I doubt any malicious app would ever let itself be sandboxed. You can use RB App Checker Lite to check the sandbox, codesigning, and other security-related states of executable code (mainly apps) on your Mac. In general I recommend using mostly apps that are designed in as secure a fashion as macOS allows.
A security feature that can stop viruses from being able to take orders from remote command-and-control servers is the built-in Firewall, also accessible from the Security section of System Preferences. For the average user, though, turning the firewall on probably isn’t really worth it. With it on, depending on its settings, every non-signed executable will need administrative authorization to accept incoming data over the internet. This isnt bad at all, in fact it is secure, but it just may become a nusiance to most users, and the security benefit probably doesn’t outweigh that. In fact, though the average user doesn’t do this, the firewall is something that’d actively hurt if you were trying to host certain services on your Mac for other computers on your network.
While viruses are something some folks worry about, they also are not the entire picture of Mac security. Another strand of security features center on actual hardware security. Unlike what I’ve discussed above both of these need to be actively enabled, and that is because they are both advanced features that do come with real downsides, especially if you aren’t careful.
Also found in the Security pane of System Preferences is FileVault. This may actually be on if you have a recent Mac laptop, as it was made default on new laptops with OS X Yosemite (well, something you could uncheck in the initial setup). This fully encrypts your internal storage device, so you’ll need a login password even just to start up the Mac. It is pretty similar to what all iOS and watchOS devices have, in that your Mac is just as encrypted as your phone. I see why Apple made this default on laptops, as those have SSDs and are quite portable, but for desktops, and anything that is purely a hard drive, it really isn’t important. On SSDs it has no performance cost, but on spinning hard drives one very much may exist. Since a login password is needed just to decrypt the internal storage, if you forget that password and also either forget your iCloud credentials or lose the recovery key (depending on the choice you make at setup) you are out of luck with no access to your files. This would make it physically impossible, or at least very improbable, for someone who steals a Mac to access its files (depending in part on the strength of the login passwords). However, the Mac needs to be shut down for the files to be fully secure, because when alive the Mac stores the encryption key in memory (though I believe that is a hidden setting that can be changed). When on the Guest User is its own special boot that provides only Safari and no access to the files on the Mac.
You can set a Firmware Password should you wish. This can be done by booting to the Recovery OS (hold down Command-R while booting your Mac) and using the Startup Security utility in the Utilities menu. What this does is set a password that your Mac, at the logic board level, will require to do anything at boot (including accessing the Recovery OS) other than booting from the internal storage. It would prevent someone who may steal your Mac from starting it up in such a way that they could erase it, or create a new admin user, or gain access to the files on its internal storage (though, FileVault does this part as well, and both features can work in tandem), etc. But it really is not something that every Mac needs on. If you forget the password there really is no way to reset it besides bringing the Mac in to an Apple Genius and presenting them with original proof-of-purchase to validate that you are its owner, as they won’t reset the password without that, and you cannot reset it yourself without knowing it.
In the future Macs will have a lot more boot-time security. The iMac Pro is at the forefront of this, with the T2 chip (a variant on the chip inside the iPad Pro) enabling advanced security. This includes the ability to refuse to boot from insecure versions of macOS, which are likely deemed any version a few months out of date after an update has been released. It can also prevent booting from external media. I hope, too, that Macs eventually gain Face ID, which also would be an advancment of general Mac security (and, given the underlying tech, possibly also ways of interacting with the Mac).
While security itself is one thing, privacy is another area that is worth paying attention to. For that I have some other tips as well.
Another thing to note and keep tabs on, across all your Apple devices actually, would be the Privacy settings. On macOS this is another tab in the Security pane of System Preferences. 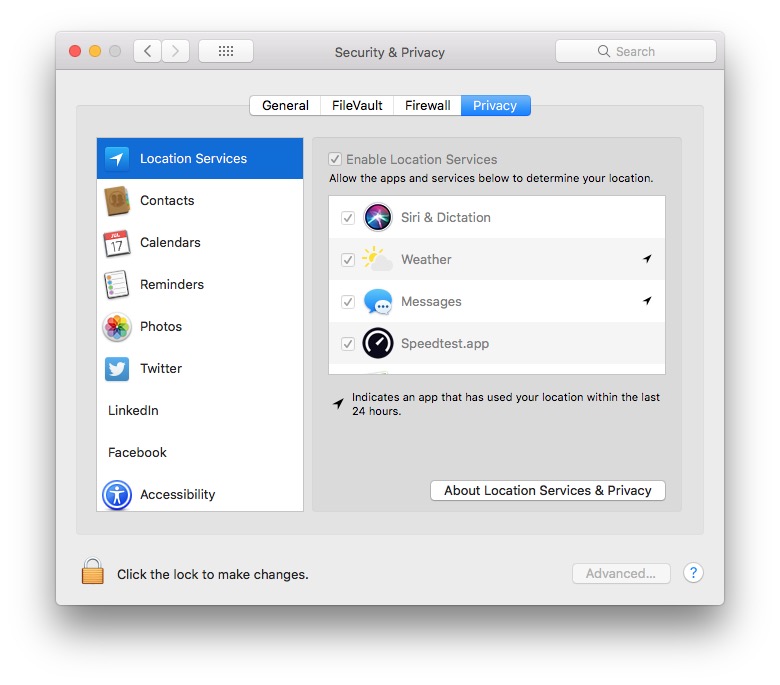 On iOS it is in the Settings app at the top level of options. Just be aware of what is allowed to access what, and especially be skeptical of apps that can see your location. You just don’t want to give away too much information. I’m not saying disable all of them, but I am saying make sure that you are aware of what the settings are, and what has access to what information.
On iOS it is in the Settings app at the top level of options. Just be aware of what is allowed to access what, and especially be skeptical of apps that can see your location. You just don’t want to give away too much information. I’m not saying disable all of them, but I am saying make sure that you are aware of what the settings are, and what has access to what information.
Similarly Safari on macOS has a tab in its Preferences window labeled Websites. This lists a series of website features that can be set per-site. Here too I recommend being especially aware of what has access to your location. I’m not saying disallow everything, but be aware of what is allowed. I recommend the default behavior for other websites to be Ask, for Location, Camera, and Microphone, at least. 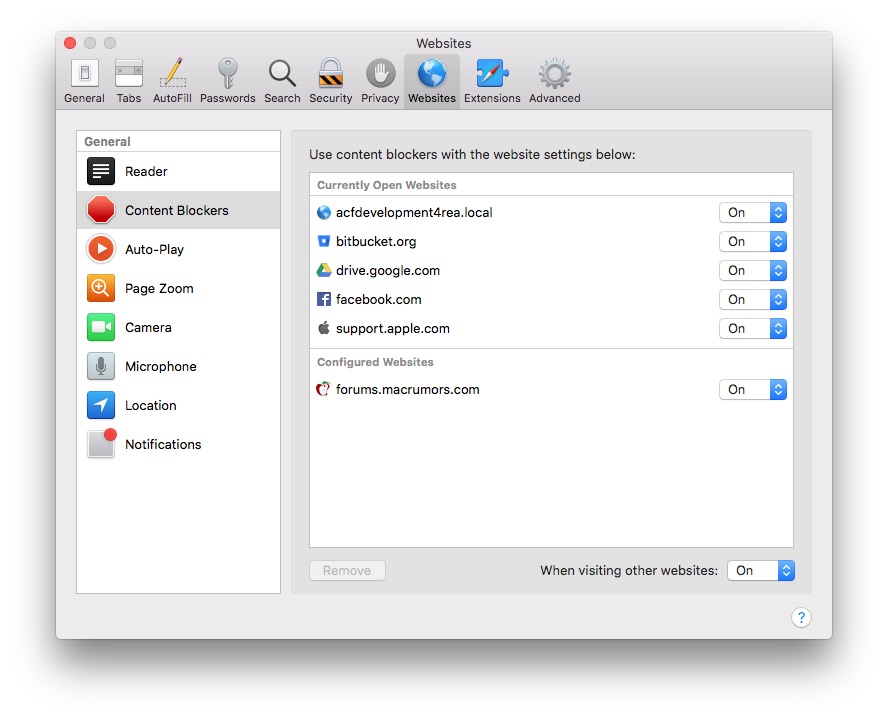 That same tab in Safari preferences would list any web plug-ins you have installed. I strongly recommend that everyomne keep the number of installed plugins at 0. Certainly, for the sake of security, don’t have either Flash or Java installed. Both have had constant security vulnerabilities. Beyond those, the more plugins you have the less stable web browsers will be. That is why I keep my Macs at a pristine state of no web plug-ins installed whatsoever. If you need a web plugin, I’d recommend that you at least make sure it is sandboxed (the Websites tab will tell you).
That same tab in Safari preferences would list any web plug-ins you have installed. I strongly recommend that everyomne keep the number of installed plugins at 0. Certainly, for the sake of security, don’t have either Flash or Java installed. Both have had constant security vulnerabilities. Beyond those, the more plugins you have the less stable web browsers will be. That is why I keep my Macs at a pristine state of no web plug-ins installed whatsoever. If you need a web plugin, I’d recommend that you at least make sure it is sandboxed (the Websites tab will tell you).
You should also at least be aware of the preferences set in the Security and Privacy tabs of Safari preferences. Also keep as few browser extensions installed as you can. Keep what you really use (like 1Password and AnyList in my case), but keep those extensions lean as well. This same basic advice flies for all web browsers you have installed.
As general communication advice, unless you go out of your way (which I very much don’t) email is in the clear and anyone can read your messages if they stumble on them. However, iMessage (the blue chats in Messages on all your Apple devices) are encrypted end-to-end, so only the members of that chat can read the contents. Keep that in mind when communicating with people. I never send passwords or other sensitive information in email, but feel perfectly safe doing so if needed over iMessage.
Another tip would be to keep tabs on what is in your Login Items list (under your user in the Users & Groups pane of System Preferences) to be sure that only the apps you know, trust, and want launching at login are listed. There are other ways for software to get itself started at boot and/or login, using a part of macOS called lanuchd, but that is trickier for average users to keep track of.
People have also asked about data security in relation to the cloud (Dropbox, Google Drive, etc.). Is it safe to store files in these services, and such. One of the questions to ask yourself is who are you trying to keep the files safe from. For the most part, unless you go out of your way, it is likely that the company running the service could access you files. Their terms of service and privacy policy probably lay out access to the files, and hopefully they only will if they receive law enforcement requests to do so. The files probably are accessible to the company. If that alone is a real roadblock then I don’t think that the cloud is for you. The exception would be if you first encrypt the files locally, like with an encrypted disk image, and then upload that to the cloud. Remember that having FileVault on is encryption of the files on your Mac, but the copies synced to the cloud (or copied to any other device) will not be encrypted unless that destination is encrypted, and are encrypted with the destinattion’s key.
Beyond that the security of files in the cloud falls onto your own account security, and being careful with only sharing documents with people that you trust. Also, if the sharing gives you the option to let others share the files, be wary of that option so that only those you absolutely trust can share files further.
I wrote an article about higher personal online security a few years ago. The advice there are the primary things to do in order to secure your cloud storage accounts:
- Strong passwords
- Two-Factor Authentication
All the cloud services that I use support Two-Factor Authentication. I strongly recommend turning it on everywhere it is offered (not just cloud services, but everywhere). Doing both of these will make it much more difficult for someone to hack into your account and subsequently gain access to your files.
Of course, the other part of securing files stored in the cloud is securing the copies you have on your devices. That is, securing your devices. The features and advice above help give you ways to do that, to whatever extent you are confortable with. Macs are inherently secure, and only moreso if you use the additional optional security features. Just, those features have downsides, so you shouldn’t enable them on a whim. iOS and watchOS devices are just as secure as a Mac with both FileVault and a Firmware Password by default and don’t have any lower security tier.
We use the cloud to store files specifically so that if our devices break or get stolen we haven’t lost the data. An added bonus is that the data is available on all of our devices. The cloud is a form of security and insurance on the data in this way. You have tradeoffs either way. If you decide that the cloud is not secure enough for your tastes then you risk data loss with device loss. Otherwise you risk data maybe being stolen with account hacks (which can be mitigated somewhat with my above advice), but can also not just access the data anywhere, but share it with those that you trust. My view is that the cloud is a very good idea and a necesary part of my digital life for these reasons, but not everyone holds those views. I admit that even I would be somewhat more hessitant to use cloud storage as much as I do if it weren’t for strong passwords and multiple factors of authentication.
Strong passwords cannot be memorized by humans, that is part of the point. Hence my advice in my other article about 1Password and iCloud Keychain. But are those secure themselves? Yes, in fact quite a bit.
Let’s tackle 1Password first. I link in my other article to their detailed description of their security archetecture. Basically, the data is all encrypted with your Master Password and Account Key. Decryption is only ever performed locally. Their website uses JavaScript, so only the specific authorized browsers can decrypt the data. Only you have access to the data stored in your 1Password vaults (or you plus others you give access to in your 1Password Team or Family), not AgileBits, the company behind 1Password.
Likewise, iCloud Keychain encrypts its data locally on devices, and the only way a new device can be accepted into the circle of trust is by an existing device confirming it, or sometimes you type in the passcode from another device on the new device. Apple cannot decrypt your iCloud Keychain. They take this circle of trust further than just your keychain, too. Health data, Siri profiles, and Safari bookmarks, maybe others, are secured using the same trust. Apple cannot see what your scale tells you, how many hours of sleep you got, or what websites you go to often.
Ultimately, though, there is only one thing preventing lapses in security and privacy: ourselves. We are the weakest link. We may reuse passwords, unwittingly download malware, or let others share sensitive files we shared with them, etc. I hope that this article gives you a better understanding of what preventative measures are in place, and other best practices, but it will still be up to each of us individually to ensure that our digital lives stay clean and safe. Feel free to add any additional suggestions, comments, or questions about this topic in the discussion area below.